
After it has been determined that a breach has taken place, there are various tasks that need to be done that are usually not in the sweet spot of the person that has been breached. Several vendors pretend they have a vertically integrated, one stop shop, solution. They don’t. They use third-party vendors who hide behind the façade of the integrated solution. If you don’t know who is doing the work, you have no basis for deciding whether you would want to use that vendor. This section highlights vendors who, through their documented business practices and/or history of exposing client data entrusted to them, have a history you should be aware of before deciding to employ their services.
1. UnitedLex
UnitedLex performs data breach reviews for several “vertically integrated” solutions, including Charles River Associates.
In 2022 UnitedLex paid, others on their behalf paid and/or they waived claims they were to be paid a total amount of approximately $30,000,000 to settle a fraud suit. The relevant news of the settlement, without mention of the waived claims of UnitedLex, is here (https://www.reuters.com/legal/litigation/leclairryan-trustee-reaches-21-mln-settlement-unitedlex-case-2022-05-17/)
For a flavor of the claims in that lawsuit, please see a relevant court filing. https://databreachtimes.com/wp-content/uploads/2023/08/United-Lex-Case-Material.pdf
In March of 2023 UnitedLex was hacked exposing client files and employee information. The manner in which they responded to the breach was consistent with their previous behavior.
Learn more
Third-Party Attacks Surge: Are Your Vendors Really Secure?
Over the past few years, The Data Breach Times has observed a surge in cyberattacks on third-party vendors. And if we think about it from the perspective of a financially motivated criminal, it makes sense. Why spend your time attacking one entity when you can attack a supplier or vendor and gain access to their clients’ data, too? You’ll not only have the vendor to try to extort, but if the vendor won’t pay your ransom demand, you can try to extort the clients.
With the surge in third-party vendor attacks, we’ve also seen increased targeting of law firms and firms that provide services to the legal industry.
In early March 2023, UnitedLex fell prey to a ransomware attack. The incident was first publicly disclosed in early April on a blog that monitors the dark web and reports on attacks. The blog reported that threat actors known as DonutLeaks claimed to have exfiltrated 200 GB of files from UnitedLex and had provided some proof of claims (POC), as illustrated in Figure 2, below.
Figure 1. D0nutLeaks added UnitedLex to their leak site on April 4, 2023. Image: <insert domainname>

Figure 2. D0nutLeaks directory of their leaked files shows timestamps of March 5 and 6. The threat actors also provided some individual files as proof. Image: DataBreaches.net.
Responding to inquiries from the blogger, UnitedLex acknowledged the breach and said they had immediately contacted the FBI and were “in constant contact with customers and employees about the incident.”
But what were they telling them? Did UnitedLex tell employees and customers that DonutLeaks had already leaked data on the dark web? Did UnitedLex disclose that a second ransomware group, AlphV (also known as BlackCat) had also added UnitedLex to their dark web leak site and had leaked a lot of data – including clients’ data?
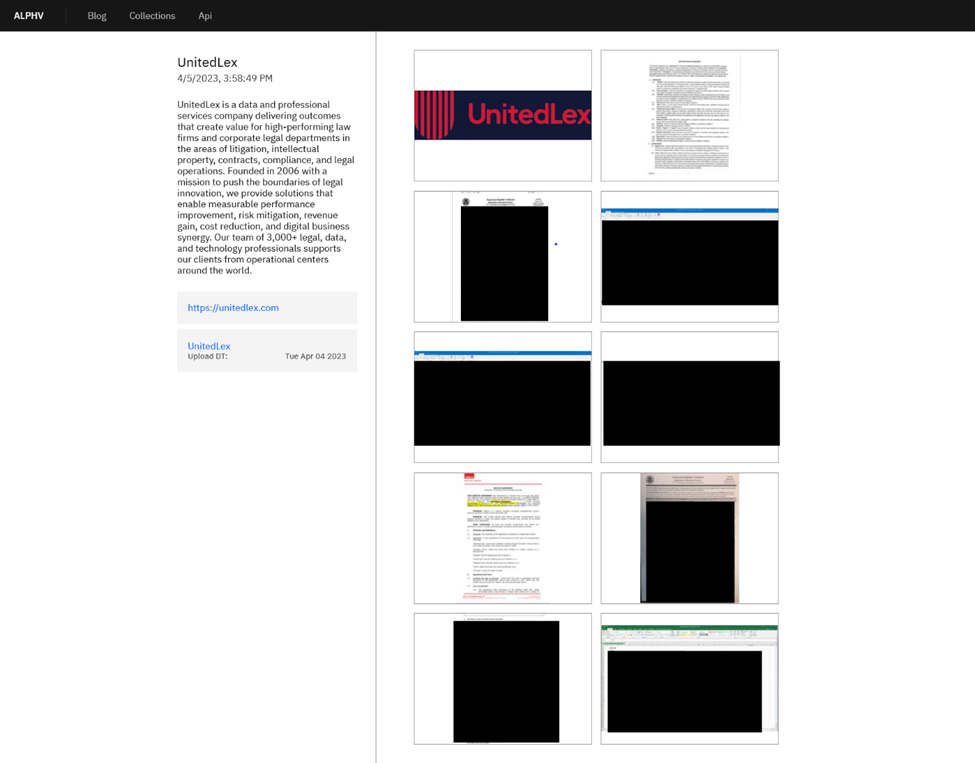
Figure 3. On April 5, AlphV added UnitedLex to their leak site. Image and redaction by <insert domainname>.
Did UnitedLex tell employees and customers that as early as March 17, a group called Monti had also claimed to have attacked them?

Figure 4. On March 17, Monti added UnitedLex to their leak site. They never leaked any data. Image: <insert domainname>
Did three different ransomware groups all attack UnitedLex, or were they just sharing data from a collaborative attack?
What were employees and clients told, and when?
UnitedLex’s notification letter was mailed on or about July 12, 2023 – four months after they detected the attack. By then, they would have (or should have) known that some client data and employee data had been leaking since early April on at least two dark web sites. Yet their letter to almost 8,000 employees does not appear to disclose that their data wasn’t just stolen but was being given away freely on the dark web. Even four months after discovery, UnitedLex noted that they were still investigating the scope of the breach to determine who else might need to be notified.
The Data Breach Times is not providing links or even screencaps of some of the leaked data, but the UnitedLex breach serves as a stark example of the extensive data loss of personal and corporate proprietary information when a large vendor suffers a breach. As many ransomware groups do when they leak data, the UnitedLex leak includes a filetree or directory of all the files on the server that were allegedly accessed or acquired. Even just skimming the list reveals many clients who had data on the compromised server(s).
On May 24, more than one month before UnitedLex sent out letters, Bell Law filed suit against UnitedLex on behalf of a former employee. Adam Behrend did not first find out about the breach from UnitedLex. He discovered that he was the victim of tax refund fraud when he went to file his 2022 taxes on April 16 and discovered that they had already been filed on April 14. Behrend later received a JacksonHewitt debit card, even though he didn’t use Jackson Hewitt. That the fraud was linked to the UnitedLex incident seems highly likely from the complaint’s statement that on April 18, Behrend also received a text message from the phone of ULX CEO Daniel Reed. The message stated that Mr. Reed had an “urgent task” for Plaintiff. “This was, of course, unusual given that Plaintiff hadn’t worked at ULX for about eight months” the complaint noted.
So months before UnitedLex sent out notification letters, at least one former employee allegedly became the victim of fraud. Someone was misusing the stolen UnitedLex data. How many more victims there might be in the immediate or long-term future is unknown to us at this point. But did UnitedLex have reasonable security in place for the data they stored? Have they complied with state laws requiring notification to individuals and/or the state within time frames like 60 days or 30 days? Have they complied with GDPR requirements for any employees and clients in the EU?
Breach notification duties are complex. UnitedLex offers cybersecurity advice and incident response services to law firms and clients in the legal services industry. Ironically, one of their articles was to make companies aware of the need to know where their data are. But do their own clients really know where their data is right now? Do their current and former employees know where their data is right now? At the very least, should UnitedLex have told them back in April that their data was leaked on the dark web?
All of this points to the question, Is UnitedLex someone you would trust with the protected information of your clients and employees?







